SecDash is an automated incident response platform, and observability dashboard. It currently listens for failed ssh login attempts, gathers intel and AI analysis against the IP address making the attempt, and drops all subsequent packets from the IP address, if recommended to do so. Have a look at it here. At the moment, login credentials are required. Anyway, here’s how it works.
Upon Logging In
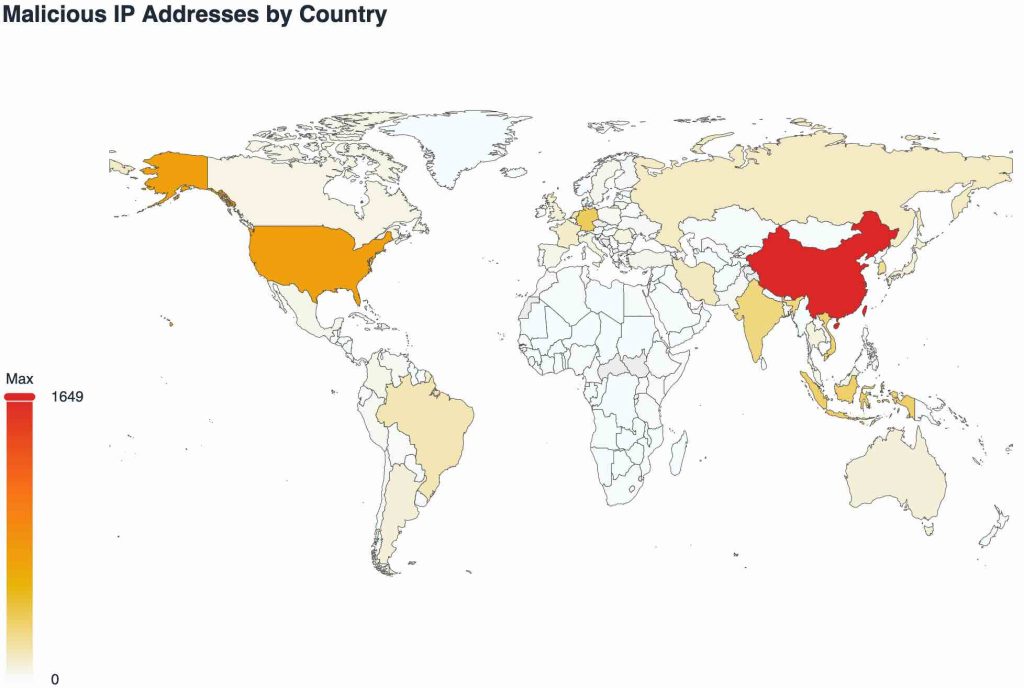
Once a user logs in, the first page that loads is a heatmap of the world that sorts malicious IP addresses by country.
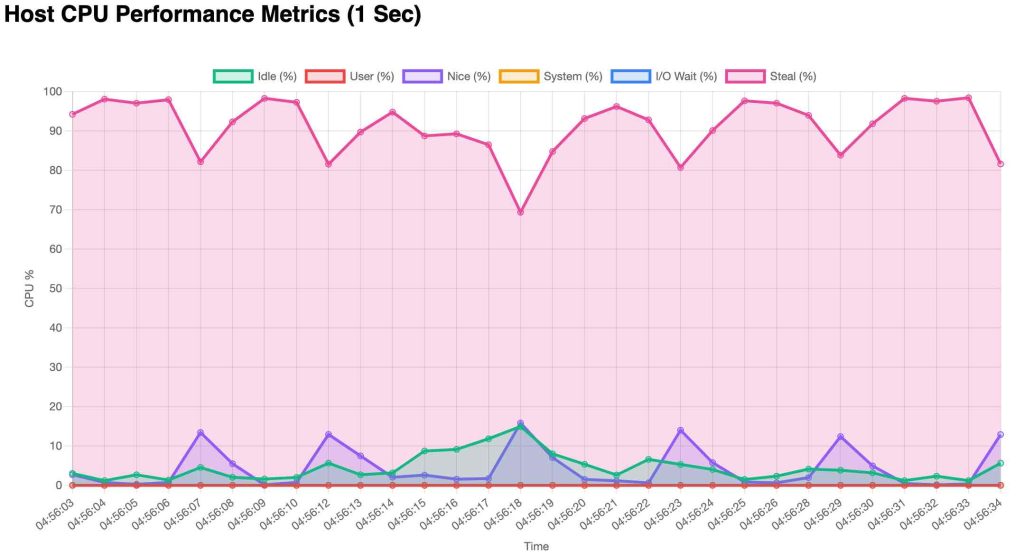
There are three additional tabs with different information. The “Host Status” tab contains a graph that displays realtime updates of host cpu performance metrics.
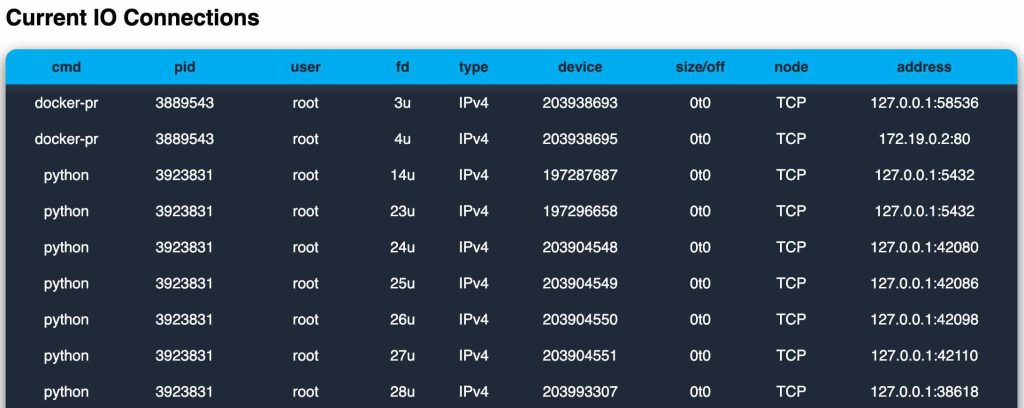
Additionally, the “Server IO Connections” tab is a live snapshot of which processes on my host are talking over sockets (mostly TCP). This is useful for tying a suspicious connection back to a specific process, and then killing the process if necessary.
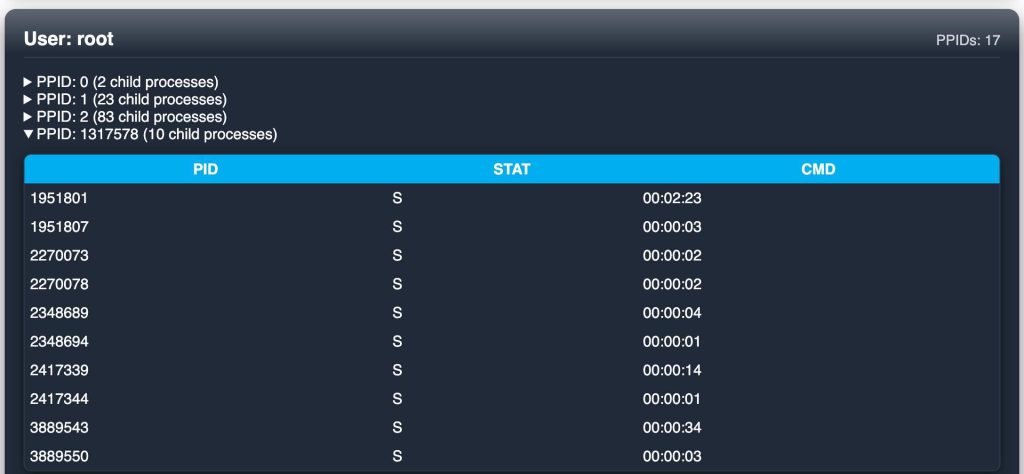
Lastly, the “Server-side Processes” tab lists out all processes by PID, grouped by user, and within each process, a table readout of each child process spawned.
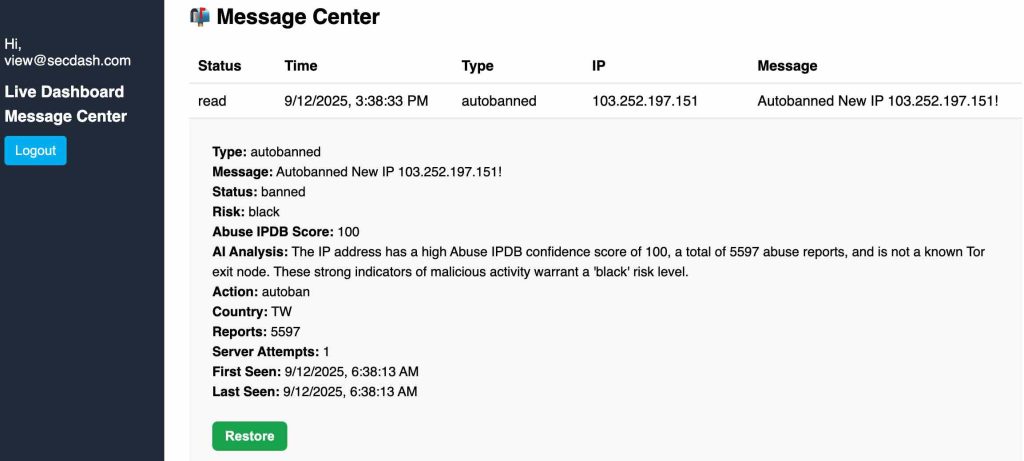
The Message Center
When the background workflow processes a new ip address, a toast notification is delivered to the frontend, and a detailed message is sent to the message center. A user can open the message, and read details regarding the address’s origin, Abuse IPDB information, the AI’s reasoning for its analysis, and the current “status”. If a user has reason to believe an address was banned in haste, he/she can remove it from the blacklist by clicking the green “Restore” button.
Logging
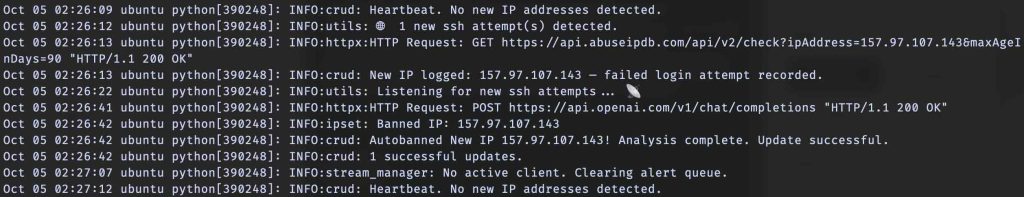
Logging is pretty basic. If observing realtime activity from the terminal, the logs notify of first-time attempts from IP addresses, additional attempts, and IP address autobans.
Data
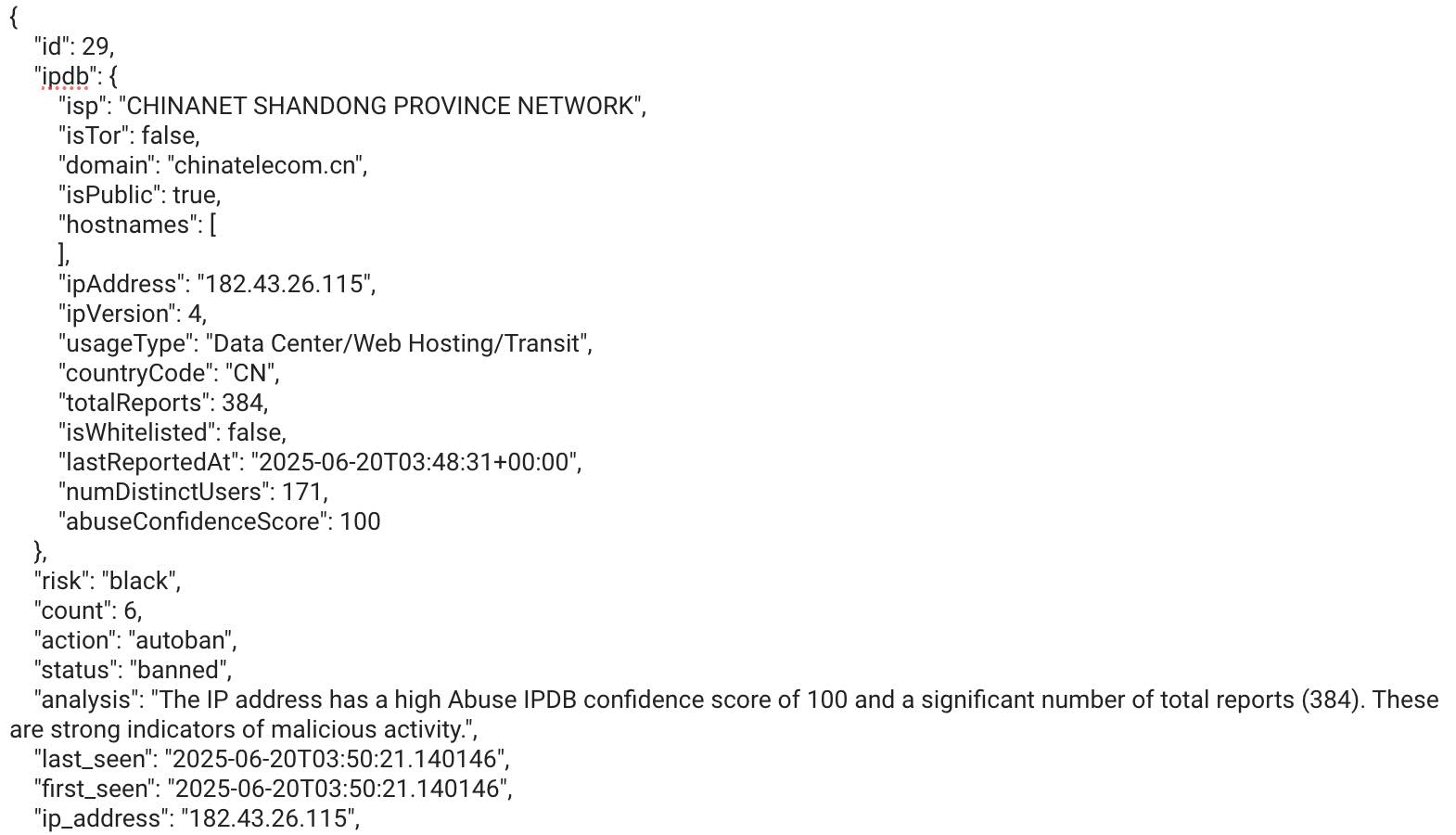
There is baseline intel gathered on any malicious IP address. The main intel is from a query to Abuse IPDB, and this is used in the AI analysis that follows immediately thereafter. Below is a screenshot that shows information gathered on a malicious IP address, which is then used to direct SecDash toward an appropriate response.
Additional Features
On the horizon? Switching from perma-ban to limited jail time, via fail2ban. Also, more observability that shows the origin of an IP address, the cidr block it belongs too, and possibly the location of datacenter that hosts the cidr blocks.